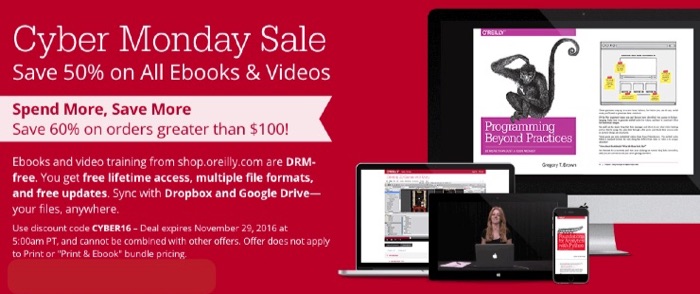
Today on CyberMonday you can buy “Seven Deadliest Unified Communications Attacks” and hundreds of other ebooks and videos from O’Reilly and associated publishers at a discount of 50% off or more. Simply go to:
and start shopping. All you do is enter “CYBER16” as the promotion code when checking out. The deal expires on Tuesday, November 29, 2016 at 05:00 US Pacific Time. Do note that this sale is for ebooks and not for the print versions of the books or for print/ebook bundles.
You can also go directly to the book’s page at O’Reilly and add it to your cart using that page.
Although the book was written back in 2010, it is sadly still VERY relevant to the Voice-over-IP (VoIP) systems deployed today. I would have loved it if vendors would have made systems so much more secure that this book could be forgotten about… but the security concerns have only increased in the time since the publication. Even six years later it still offers relevant advice and suggestions about how to make sure your IP communication systems are as secure as possible.
I am a big fan of buying ebooks directly from O’Reilly because doing so gets you:
- DRM-free – no stupidity with license restrictions.
- Free lifetime access
- Multiple formats (ex. ePUB, PDF, Kindle, etc.)
- Free updates
- Sync with Dropbox, Google Drive and other similar services
… and more!
FYI, I recorded a short podcast episode about this sale:
P.S. My “Migrating Applications to IPv6” book is also on sale as an ebook at O’Reilly’s site… if you are interested in how to make sure your applications can work over IPv6, please do check that book out, too.
 Want to lean more about how to increase the security of your unified communications (UC) / voice-over-IP (VoIP) system? Today you have a great opportunity to buy “Seven Deadliest Unified Communications Attacks” and hundreds of other ebooks and videos from O’Reilly and associated publishers at a discount of 50% off or more. Simply go to:
Want to lean more about how to increase the security of your unified communications (UC) / voice-over-IP (VoIP) system? Today you have a great opportunity to buy “Seven Deadliest Unified Communications Attacks” and hundreds of other ebooks and videos from O’Reilly and associated publishers at a discount of 50% off or more. Simply go to:



